
Some of you know from my past blog posts and emails that the Russian Federation is one of the most prolific sources of hacking against websites and social media platforms. Not just in Europe, but here in the U.S. as well. This includes what most refer to as “social engineering,” which means they have created fake accounts to change the social and political narrative about what they are doing in Ukraine and why they are “protecting” the native Russians who now live in Eastern Ukraine. Ostensibly they flood social channels and website “comments” sections with their own characterization of their scheme, spoofed to look like these accounts, and usually most of the “likes” and comments appear to come from legitimate sources.
A Large Increase in Website Attacks from Russian Sources
While we’ve always tracked a very high level of attacks against our client’s websites sourced from the Russian Federation, over the last few weeks my alert notifications indicate a dramatic increase in Russian-based attacks that we categorize in these buckets:
- Brute Force – these are the hardcore user name- and password-guessing crunching, starting with email addresses, nick names, company names and a host of other frequently used shortcuts that many users employ so they don’t forget their login credentials. Brute force attacks are heavily driven by bots that bang on the website in a persistent way, unless there are “caps” put on failed attempts that permanently block those source IP addresses. That’s exactly what we use in our security protocols, setting up a maximum number of failed attempts before a source IP address is blocked.
- Complex – these are attacks against hosting site databases, plugin “holes” or outdated versions of hosting platforms in which a breach can allow ransomware, malware and spam redirection code to be inserted into the hosting platform’s software, and then use that server for future attacks against other websites, or to redirect spam emails that protect the identity of the sender and the sender location.
- Blocklist – our security software maintains a block list of IP addresses that have already been blocked by our software, or manually by the CommLinks team, when we see those IP addresses used to spam or scam or hack our clients’ websites. We also integrate with our security software’s master blocking list tables that are shared across all four million sites protected by the security software company we use.
Unfortunately, I see this enormous lift in attacks across the board on the 50+ sites that we manage and protect. While we know the U.S. banking system, electrical grid, city government websites and even Federal agencies are attacked frequently (especially now), why hit everyday websites of golf courses, resorts and other lesser-trafficked websites?
The main reason is that many of these websites are not protected by security software. Some less experienced web developers and IT managers aren’t diligent, so user names and passwords are weak and can be very easy to crack. Yes, “admin” and “12345” are used more often than you can imagine. One hacker goal is to hack into these sites to install malware and/or ransomware to disrupt commerce. Another goal is to insert redirection scripts that enable hackers to bounce spam/spoofed emails off one of our client’s web hosting servers so the true source of spam is harder to trace. And, a more malicious goal is to scrape user profiles, credit card information and login credentials for future use in creating chaos at the individual user level. How many of you use the identical password for multiple websites? If a hacker gets that frequently used password, they’ll load that into a bot and hit many sites to see if that password lets them into one of your online accounts.
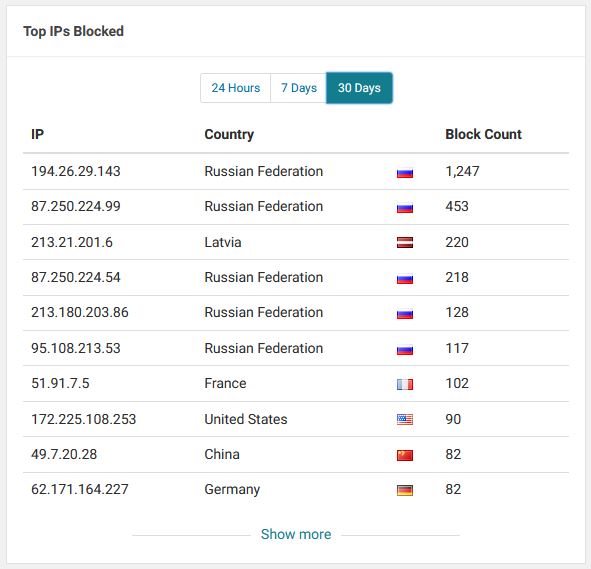
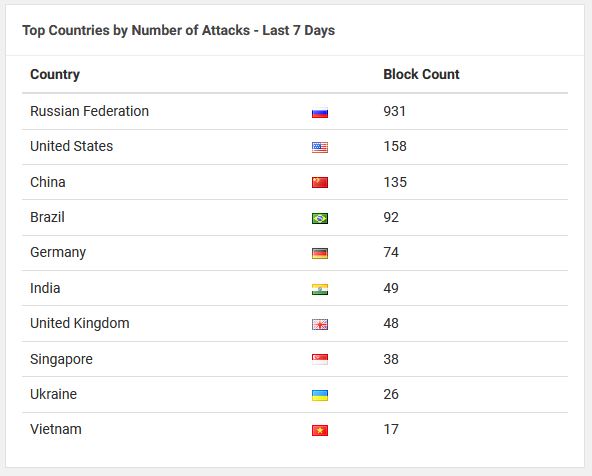
Below we’ve pulled a couple of security software images from two of our clients’ websites. These were scraped as of this morning. Each image is but an example of many more visual data widgets that we review each day in the WordFence security dashboard to look at sources and trends in hacking attempts. The image on the left is for Client 1 and shows you the number of hacking attempts by Top 10 IP Addresses – Last 30 Days. The image on the right is for Client 2 and represents the Top Countries by Number of Attacks – Last 7 Days.
A common theme? The Russian Federation!
Client 1 Website
Client 2 Website
How Does Communication Links Protect Your Site?
We use WordFence security software on our client websites. While it is an extremely powerful and well-documented success in fending off attacks, a Distributed Denial of Service (DDoS) attack can still be disruptive by sending thousands of bots to hit sites at the same time, potentially bringing the websites down. The source IP addresses of these attacks are captured and added to our blocklist tables, but the immediate outcome is disruption. Russia has some of the best hackers in the world, and they are state-supported bad actors whose mission is to let ground troops pound buildings, bridges and such from the outside, while hackers break into and disrupt financial institutions, communications, media outlets and government agencies through cyber warfare.
This morning, WordFence distributed an informative security blog post to its client database about what they are seeing from Russia as it attacks the Ukraine. If you are interested in cyber warfare and its impact on our country, it is well worth a read.
In Wordfence’s CEO blog post, Mark Maund makes a reference to something that we see almost every day in our inbound emails, or those emails that hit our junk mail folder here at Communication Links: phishing emails disguised as legitimate emails from Amazon.com, Chase Bank or from a “friend” you haven’t heard from in a long time. The way Mark phrases it is worth remembering:
“Ask your team to be on the lookout for anything that “seems weird.” Adopt an approach of “If you see something, say something” and at the very least you’ll have an interesting discussion – and at worst, it’s an attack underway.”
And, to add to that, please do NOT click on links that appear “weird.” We’ve also seen a rapid escalation in client website contact forms containing obvious phishing URL links embedded into the contact form comments box. If you see an embedded email address or website link ending in “.ru” (Russia), delete it immediately. It is NOT a tee time booking confirmation! 🙂
As always, when you are on the Internet remain alert to what you click. And, if anything looks strange and you need help, please don’t hesitate to give me a call or drop me an email if we can help.
