
On March 10, 2020, Tom Burt, a cybersecurity executive at Microsoft, released a blog post about a significant step taken to corral one of the most prolific botnets we’ve ever seen. In coordination with worldwide ISPs, domain registrars and with court-approved action, Microsoft led the dismantling of the Necurs botnet which was run on up to 9 million infected computers worldwide.
Here’s his blog post if you are interested in what reads like a spy caper please.
As expected, the Russian Federation is at the center of this sophisticated hacker ring. The person or persons running the botnet participated in distribution of malware, ransomware, phishing scams and spam on an unfathomable scale. Tens of billions of attacks have been generated through this botnet, and by securing the US-based portion of their infrastructure, Microsoft itself has helped bring down this cyber-crime ring. Other agencies worldwide managed local elements in their respective countries to disrupt the organization’s illegal activities.
My Website Is Insignificant Globally - Why Should I Worry?
What does this mean for our clients? We manage over 60 client websites and employ a series of scripted auto-responder alert messages sent directly from our hosting platforms back to us should one of our managed websites come under attack.
Do they? Yes, unfortunately they do. Over the last 7 days, these images below show you a visual log of just two of our managed websites. These represent the Top IP addresses from which botnets have attacked these client websites. If you see similarities in the IP addresses, that’s because the IP addresses represent websites from which large-scale attacks are distributed on a global scale. All of these attacks were successfully blocked by the web application firewall (WAF) software we use to protect our client websites. And, we also add permanent IP address blocks so these particular IP addresses can’t be used to launch subsequent attacks.
Regardless of our efforts, attacks can compromise older websites, especially those with outdated plugins, soft passwords or operating on older versions of hosting software that can’t be updated for one reason or another. We can usually mitigate a hack through backup restoration. But, often, rebuilding a website on safer hosting platforms is the most expedient defense.
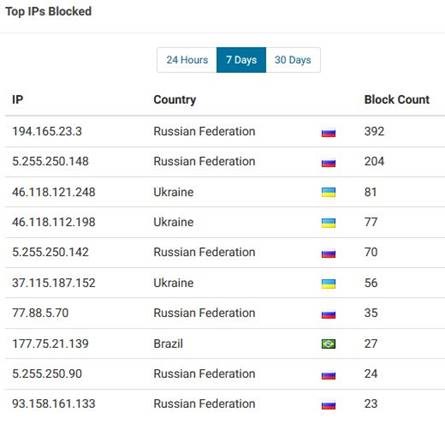
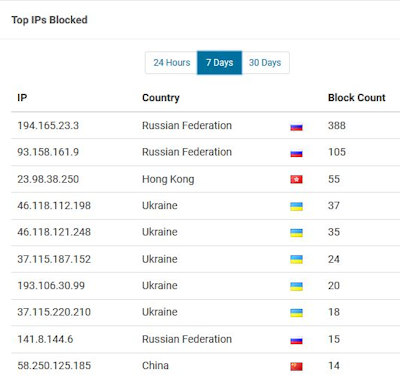
Every Client Website Is Important to Us
We don’t believe that any client websites is insignificant or that it flies under a hacker’s radar. Whether the website has 500 website visits per day or 50,000, the point is that public websites can be a target for hackers and their malicious bot swarms. What attackers want to do is scrape any data they deem of value (credit cards, personally identifiable information, etc.). If nothing of magnitude exists on that website, then they want to insert code to infect the server so that it can become a vessel and proxy through which the botnet can spread to other computers.
We protect each site with a focus on hardened login credentials, daily backups of website files, updating plugins and server software, and quickly responding to security alerts when one of our client sites comes under attack. By taking down the Necurs botnet, the short term impact should be that many of the coordinated botnet attacks we’ve seen on the client websites should subside.
The problem, of course, is that hackers don’t really stop what they are doing. They pivot by restarting their efforts, sending out small swarms of bots to begin creating a new network of infected devices. However, global domain registration companies are certainly on notice through Microsoft’s actions to not blindly issue new domains without some buyer profiling to ensure the legitimacy of the domain registrant. ICANN and other organizations control the domain registration process, so with some successful, global collaboration they can hopefully put a dent in hacker activities over the near term.
